You do you and we’ll secure The remainder with our obtain and security ensures. And For those who have any inquiries, our security gurus are available 24/seven that will help.
For your past 10 years, this group of FSB hackers—including “traitor” Ukrainian intelligence officers—has made use of a grinding barrage of intrusion strategies for making lifetime hell for his or her previous countrymen and cybersecurity defenders.
Rashmi Ramesh • April 22, 2025 Generative synthetic intelligence assistants guarantee to streamline coding, but large language models' tendency to invent non-existent offer names has brought about a brand new supply chain hazard often called "slopsquatting," wherever attackers sign-up phantom dependencies to slide malicious code into deployments.
The China-dependent Winnti Group has released a marketing campaign referred to as “RevivalStone,” focusing on Japanese businesses from the manufacturing and Electricity sectors with State-of-the-art malware and WebShells. The attack highlights the necessity for robust cybersecurity defenses versus condition-sponsored threats.
Plankey isn’t new towards the Trump administration, as he Formerly served because the principal deputy assistant secretary on the Section of Electrical power from 2019 to 2020. He also labored since the director for cyber coverage with the National Security Council prior to that.
The CVE Software is the key way program vulnerabilities are tracked. Its long-phrase long run remains in limbo even following a very last-minute renewal of the US governing administration agreement that funds it.
Not essentially. The better EDRs will most likely detect the majority of industrial infostealers, but attackers are frequently innovating, and particularly, extra refined and well-resourced risk teams are recognized to establish customized or bespoke malware offers to evade detection.
Ever heard of a "pig butchering" rip-off? Or a DDoS attack so significant it could melt your brain? This 7 days's cybersecurity recap has everything – govt showdowns, sneaky malware, and in some cases a sprint of app retail outlet shenanigans.
Protected our globe jointly Assistance educate Every person as part of your organization with latest cybersecurity news cybersecurity awareness methods and coaching curated via the security specialists at Microsoft.
How much time does it just take for McAfee to eliminate my knowledge? Time it will require to eliminate your individual information will range according to the location. Most will eliminate your own facts within two weeks, Although some can take around 45 times.
A Python script using the tkinter library produces a faux “Blue Monitor of Loss of life” (BSOD) being an anti-Investigation tactic, disrupting devices temporarily though evading antivirus detection as a consequence of its lower-profile nature. Behavioral Investigation is essential for pinpointing these kinds of threats early on.
Adhering to this incident, James alleges Countrywide Normal “ongoing to go away driver’s license quantities exposed” with a separate Web site, which allowed hackers to obtain ahold of the personal information of greater than 187,000 clients the following calendar year. She also promises Nationwide Standard did not effectively notify impacted clients.
Allegedly responsible for the theft of $1.5 billion in copyright from one exchange, North Korea’s TraderTraitor is Probably the most subtle cybercrime groups on the globe.
"Legacy excuses are infosec news out; the globe has zero tolerance for memory-unsafe code in 2025," Abbasi said. "Sure, rewriting aged methods is daunting, but letting attackers exploit many years-aged buffer overflows is even worse. Companies nevertheless clinging to unsafe languages chance turning small vulnerabilities into enormous breaches—and they can't claim shock. We've experienced demonstrated fixes for ages: phased transitions to Rust or other memory-Safe and sound selections, compiler-level safeguards, thorough adversarial tests, and community commitments to some protected-by-design roadmap. The real challenge is collective will: leadership need to need memory-Secure transitions, and software program buyers have to hold suppliers accountable."
 Spencer Elden Then & Now!
Spencer Elden Then & Now! Jonathan Lipnicki Then & Now!
Jonathan Lipnicki Then & Now!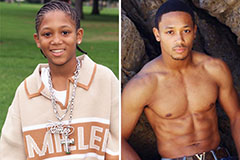 Romeo Miller Then & Now!
Romeo Miller Then & Now!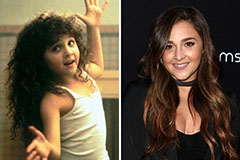 Alisan Porter Then & Now!
Alisan Porter Then & Now! Jennifer Love Hewitt Then & Now!
Jennifer Love Hewitt Then & Now!